TunnelBear displays statistical data concerning the trackers (analytics, ads, scripts, social buttons on Facebook, Twitter and LinkedIn) blocked by the application during your browsing session. It features desktop notifications to let you know about important events, while the 'Vigilant mode' is capable of adjusting the security level.
Automation Solution based on vehicle license plate recognition technology (ANPR). Software reads vehicle license plate from video stream. Ideal for access control and pass control solutions. Additional included features: Black list module, Barrier control module.
File Shredder is a small utility that will completely erase the contents of sensitive files and folders that you specify. Normal file deletion only removes a file's directory entry, but leaves the data contained in the file on your disk drive. File Shredder completely overwrites the contents of a file and then deletes it. To shred files and folders simply drag them to the File Shredder icon in the same way you would the Recycle Bin.
Sismaâ„¢ is an easy-to-use password manager that allows you to store and manage your passwords in a secure and convenient way. Sismaâ„¢ keeps your accounts details and passwords in a secure database that is encrypted with strong 256-bit Advanced Encryption Standard (AES, Rijndael) cipher. Sismaâ„¢ includes a strong random password generator which can generate alphanumeric or pronounceable passwords.
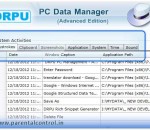
Comprehensive Download Parental Control application enables user for recording incoming, outgoing and composed emails event performed by user on windows installed notebook. Website offer advanced PC monitor utility enables you to records whole personal computer activities performed by your child. Innovative parental control software facilitates user for controlling entire clipboard contents and screenshots event for a fixed time of interval.
This is a very simple and fast program will help users to perform a Chrome password recovery. It is well known that the browser Google Chrome can save usernames and passwords for different sites. The user can view them in your browser settings if some computer skills. But very often novice PC users are asking how to view saved passwords Chrome exactly where to look for them?
Are you worried about privacy? Do you know that GMail, Facebook and others online services, automatically reads and scan your messages for advertising purpose? Free Message Encrypter is for you! Free Message Encrypter automatically replace your message with an encrypted one!
Encrypt and decrypt whole files or their parts using AES, Triple-DES (3DES), RC2, and DES symmetric algorithms. You can encrypt files with a single password or specify cryptographic keys (vectors) instead. You can change key bit length for better protection. You can select specifically which bytes in a file should be encrypted/decrypted, though by default the whole file is processed.
BestCrypt automatically encrypts data before saving or storing a file. Sensitive information is scrambled using an algorithm, making the data unreadable. BestCrypt will transparently decrypt the file once the file has been opened by providing the correct password or key.
Command-line Tool to find and display PEB Address of Process
Cant remember your passwords? Tired of typing your name and address into internet forms? ... You need WebM8! - WebM8 will remember all your usernames and passwords and fill your log on screens automatically. It will also allow you to fill other web forms by point and click and, unlike most password programs, it is completely browser independent and suitable for logon forms which change each time you use them.